8. Surveillance
Laura Matson and Steven Manson
We live in a surveillance society and always have. Multiple organizations track our daily activities, and often with the help of geospatial technologies including mobile phones, satellite remote sensing, and sophisticated mapping systems. The practice of tracking populations is not new. Governments in particular have long conducted surveillance of individuals and groups for centuries, although they have been joined by a host of companies and other groups. For most of human history, however, surveillance was limited in scope because it required a lot of human resources. The advent of computers and computing networks has vastly expanded the ability of government agencies, commercial firms, and other organizations to monitor millions of people.
This chapter will introduce you to:
- Surveillance as a concept that has long been a part of human societies
- Drivers of the new surveillance society
- Surveillance from both the inside and outside of our daily lives
8.1 Surveillance
In many ways, we are living in a surveillance society and have been since the earliest of human civilizations. Multiple organizations track our daily activities, often with the help of geospatial technologies. The practice of tracking populations is not new. Governments, in particular, have long conducted surveillance of individuals and groups, and many countries have conducted a population census continually for centuries. From the 1800s onward, most governments have tracked their populations. Besides basic demographics, governments gather health surveys, migration information, data on border crossings, crime, and more (as seen in the map below).
For much of human history, the opportunities for surveillance were physically bound in important ways. For example, governments have always employed people to follow other people around to keep them under observation, but this is expensive and time-consuming. It is also difficult to monitor people passing across borders or to count citizens once a decade at their home via a census. This kind of door-to-door census is tremendously costly to conduct because it involves paying thousands of enumerators to go to homes and talk to people in addition to the money and time spent mailing, reading, and tabulating surveys. Since around the mid-Twentieth century, however, technology has made it much easier for governments, companies, groups, and individuals to surveil large numbers of people.
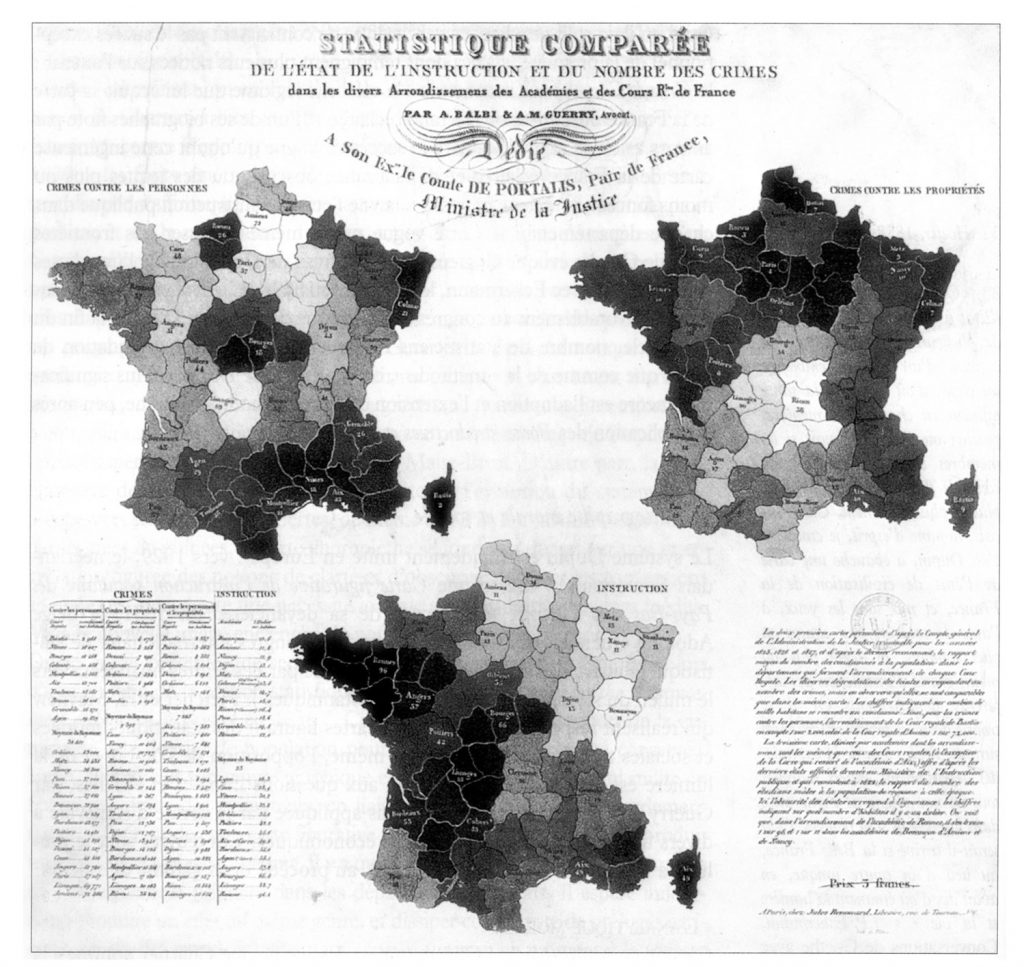
State surveillance. Map of crimes against persons, crimes against properties and education in France (1829). Governments gather information on health, migration, crime, and more/. [1]
There are three recent drivers of expanded surveillance, which threaten to fundamentally rewrite the rules about how government agencies, commercial firms, and other organizations keep tabs on individuals.
The first major driver is our ever-improving technology which has become less expensive and much faster.
- Computerization. From the 1940s onward, the advent of computers heralded new capacities for observing and tracking societies. Computers are very helpful for keeping records and making connections among records, and they can store large amounts of information.
- Networks. From the 1980s onward, communication networks made it easier for computers to talk to one another. Organizations could share information more easily and it became easier to collate information from many different places.
- Miniaturization. Both computers and networks benefit from miniaturization. Computers are becoming faster and networks are becoming almost omnipresent. Mobile phones exist because computers are now small enough to fit in your pocket while remaining capable of networking with other computers.
The second driver of expanded surveillance is the rise of the politics of fear and security. Although by most measures we are living in a safer world than ever before, many people feel less safe and less secure than in the past. The reasons for this mismatch are numerous and complex, but in general, there is evidence that bad news travels faster than it ever has before. The news is filled with stories of danger and tragedy from around the world, stories we would not have heard about by just relying on the newspaper or evening news. We have also seen an increase of, and desire for, a range of surveillance technologies, such as cameras put in private and public spaces in the name of safety.
These technologies are arguably making us safer in some cases, but at what cost to personal liberty and privacy? These trends are also related to both perceived and actual increases in terrorism, along with related threats such as cybercrime. This has ushered in a new era in which governments have sought more powers of surveillance. The Patriot Act in the US, for example, substantially increased the powers of government to track citizens through their phone records and online activities, often with little or no oversight. While these measures have undoubtedly helped protect people from harm, they have also introduced a new and potentially dangerous level of government scrutiny into the lives of all people.

Surveillance cameras. These cameras have become ubiquitous. This one is part of the Memphis Police Department’s Blue Crush Taking Back Our Streets initiative. [2]
The third major driver in the growth of surveillance is the personalization of tracking. In general, we have moved from a situation where a person was observed or tracked in one or two places, like at a border crossing, to a situation where a person can be observed directly or indirectly at almost all times. In some cities, a person can be seen by dozens of cameras a day and their face or license plate number can automatically be matched against databases. Essentially every online interaction you have, be it looking up directions on a map or looking at shoes on a website, is tracked by multiple organizations, ranging from private sector companies to government agencies. If you carry a mobile phone, you are also carrying a device with a microphone, camera, and location tracker. These are just a few of many possible examples of the ways in which you are monitored on a regular basis.
8.2 Inside Surveillance
Often we think of surveillance as happening outside of daily life – we watch movies where secret agents use satellites, telescopes, and microphones to spy on criminals or enemy agents or our hapless heroes. Really, though, much of the surveillance we experience is “from the inside,” in that we willingly purchase spy gear and carry it with us in order to be spied on.
Many of our possessions, including clothing and other items we buy in stores, have radio-frequency identification (RFID) tags built into them, which can continue to be accessed even after their original purpose has been fulfilled. These RFID tags help to prevent shoplifting, but it is possible for anyone to read these chips; so, for example, if you buy a pair of jeans from the Gap, another retailer could read the chip in your jeans months later. Companies constantly experiment with different ways of using these and other kinds of technologies. Your student ID card likely has an RFID chip embedded in it, as do many of the cards you carry. These chips are helpful because they allow users to open locks and doors with the swipe of a card instead of having to use a key for every door. Some universities have gone a step further, however, and have installed special doorways that detect students’ IDs automatically. They are experimenting with using this technology to track attendance in classes, use of the cafeteria, or to make for easy entrance to dorms. Of course, you can imagine many other uses to which this system could be applied. How would you feel knowing that the university knows your every move on campus?
Our mobile phones are tremendously useful, but many different parties – phone companies, marketing firms, government agencies – have varying degrees of access to the microphone, camera, data, and location of your phone. These organizations know who uses the phone, what they use the phone for, and where the phone is at all times. One advantage of this situation is that companies can offer location-based services (LBS), or services and products that take into account where you are. If you search for a coffee shop, for example, your phone will tell you the locations of the nearest shops, give you ratings, and provide directions. Of course, companies like Google or Apple provide search results that are biased toward stores or chains that pay advertising fees. They are also interested in tracking the people you spend time with; features such as facial recognition or the opportunity to ‘tag’ or identify friends and family in photos are often billed as a great way to help organize photos, but they also provide a way for companies to better understand your social networks.
Most of our activities online are tracked by companies and governments. There is always a tug of war occurring behind the scenes over the balance between protecting the privacy of people being tracked versus using this tracking information to learn about people, their activities, and their relationships. The companies that power the internet, such as Google, Apple, and Facebook, keep track of every person who uses their services. They track what you buy, with whom you communicate, the stories you read, and the people with whom you associate. Much of this is spatially-aware knowledge, in the sense that these companies can track with whom you travel or spend time.
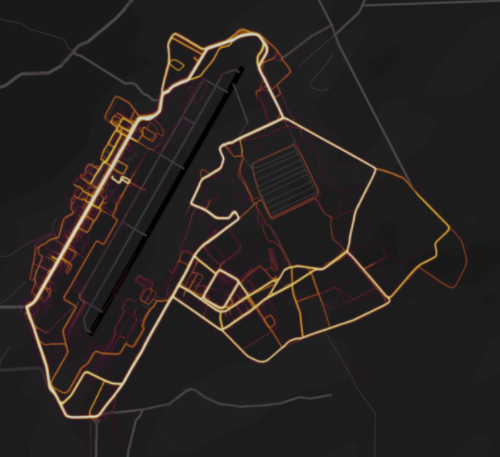
One side effect of many people being tracked is that this continuous and automated collection yields a lot of data that can be used in various ways, some inadvertent. These data are typically used by companies to develop better products and sell advertising while providing a useful service. There are many mobile phone applications (or “apps”) on fitness, for example, that will use your location to help you plan running or biking routes, monitor your exercise routines, or encourage you to push yourself further. Strava is one such application that is used by millions of people around the globe. In addition to using the data for its own purposes, the firm shares its data as maps. One unanticipated side effect of this data sharing is that it became apparent that members of the armed forces and security services of various countries were using the app and inadvertently sharing their data. These data could be used to create high-resolution maps of how, where, and when people moved around on a military base such as the Bagram Air Base, the largest U.S. military base in Afghanistan, pictured here. This level of specificity poses a range of security risks. This is just one example of the many potential uses and misuses, inadvertent or otherwise, that may result from the mass surveillance of people using their mobile devices.
Mobile phone tracking. Users of a fitness app shared their locations and these data in turn were used to make a map that showed details of a military installation. [3]
Most transactions have some sort of receipt or indication of their occurrence and we have many different kinds of records about who we are and what we do: internet activity, credit card purchases, debit card activity, airline tickets, car rentals, medical records, educational transcripts, driver’s licenses, utility bills, tax returns, and records of most life events, including birth, marriage, divorce, and death. These records are collected and collated by governments and private firms, and other organizations. Government agencies, political parties, advertisers, and internet companies like Google or Facebook are just a few of many organizations that maintain vast amounts of information on individuals from the moment they are born until when they die. It is very difficult for individuals to gain access to these data or learn how they are used.
Much of the time, this tracking occurs with our blessing: we choose to be tracked in order to get better search results, deals on services, travel directions, and so on. There are other times, however, when these data are misused to breach the privacy of individuals, or when they are stolen by cyber-criminals and used to commit fraud. These same dynamics also hold true for governments. Local, state, and federal authorities use cell phone information in various ways to help catch people suspected of crimes, but these technologies are often also used to monitor citizens for potential criminal behavior. There have been many, and will likely continue to be many, instances where these data are misused by trusted authorities in ways that skirt or sometimes just break the law.
Beyond our phones, there are a variety of ways in which computers, networks, and miniaturization have made it easier to track people. GPS receivers are small and powerful, making it easy for security or investigative agencies to place them on a suspect’s car or person and track them for months. Insurance companies offer drivers the opportunity to have GPS trackers placed in their cars in order to get a better idea of how a person drives, which can lead to better rates – at the cost of having a company know your every move. Many new cars have GPS-based services built-in, such as emergency roadside assistance, which can be a real help when you have car trouble. These companies often sell this information, however, to other companies that want to know where you travel or where you live.
These are just a few of many examples of how we are all tracked in the course of our daily lives.
8.3 Outside Surveillance
A growing amount of surveillance also happens from “the outside,” by which we mean when you are being observed or tracked in ways that do not rely on devices you carry on your person or are derived from your interactions with computers.
A prime example of surveillance from the outside is remote sensing technology, which is rapidly improving. Until recently, the spatial resolution of these sensors was not good enough to see or track people, but now there are several companies and governmental agencies that offer space-based and airborne sensors that can track individual people and cars with ease. Some commercial systems can track every single person and car in a city over the course of hours, and military and government systems are much better. Military-level surveillance techniques can even be applied to, for example, apprehending suspected criminals in US cities or tracking literally thousands of cars at the same time as they move along city streets.
More prosaically, most cities are carpeted with surveillance cameras mounted on any number of objects – stores, houses, light poles, or traffic signs. There are some urban areas where you cannot walk virtually anywhere without being captured on camera. For some people and places, these cameras are seen as a good thing. The site www.videosurveillance.com/communitycam/, for example, argues for more, and better camera coverage in order to safeguard property and protect people from harm caused by crime or automobile accidents. In contrast, the New York Civil Liberties Union’s Surveillance Camera Project warns of the dangers of blanketing cities with cameras, especially in how they offer security but at the cost of intruding into the lives of many people by removing their ability to be anonymous, move through the city freely, and associate with other people without fear of being watched.
Another emerging technology that is both useful and troubling is facial recognition. Many of the kinds of data collected about people during the course of their daily lives can be associated with them because they carry a phone or use a computer. In other words, surveillance from the inside. Leaving a phone behind or not using a computer can free a person from this form of surveillance, but it does not prevent other people from taking photos of that person or from cameras from doing so. Increasingly, these photos and videos are processed by computers that can recognize faces and associate these faces with other records. Apps on your mobile phone, like Facebook or Google+, can automatically identify the people in your photos. We are very close to a time when someone can simply point a phone at you and be able to bring up all sorts of information about you without your knowledge and consent.
Consider a program being tested in China, called “Xue Liang” or “Sharp Eyes”, a nationwide surveillance system that uses artificial intelligence to match people from a photo database to the video feeds from private and public cameras in streets and in homes and businesses. This system is seen as being helpful because it would allow banks, hotels, airports, apartment buildings, schools, and other places to identify people and allow them entry automatically. Of course, the police and security forces are also very interested in being able to track actual or suspected criminals. Further plans include linking this facial recognition system to medical records, social media posts, travel plans, and purchases in order to create a single system of pervasive and ubiquitous national surveillance. The program will eventually give officials the ability to track what people are doing, where, and with whom.
Perhaps the fastest-growing form of surveillance from the outside is one that is also much like surveillance from the inside namely the profusion of internet-connected devices such as baby monitors and internet-enabled speakers like Google Mini or Amazon’s Alexa or Echo. These are devices that are always on, always listening and watching, and always feeding information back to their companies. Of course, people have these devices in their homes because they are helpful—they can search the internet, order groceries, and monitor whether a child is sleeping peacefully. These devices also have drawbacks. Companies record and track every utterance or request, feed this information into their systems in order to use it both in house, and to sell to other companies. Many of these devices—especially cameras and toys—are incredibly insecure and are vulnerable to being hacked or taken over by people in order to spy on you and anyone else who is in your home.
Even when organizations don’t have pieces of information about you, in particular, they can make very good guesses about the sort of things you do, buy, and want based on where you live—with even small amounts of information. This way of combining location with attributes of the people who live in a given place is called geodemographics. A product by Esri called “Zip Tapestry” divides the country up by zip codes and other zonations, and then describes a good guess about who lives in each area. You can try it yourself at ESRI’s Zip Tapestry.
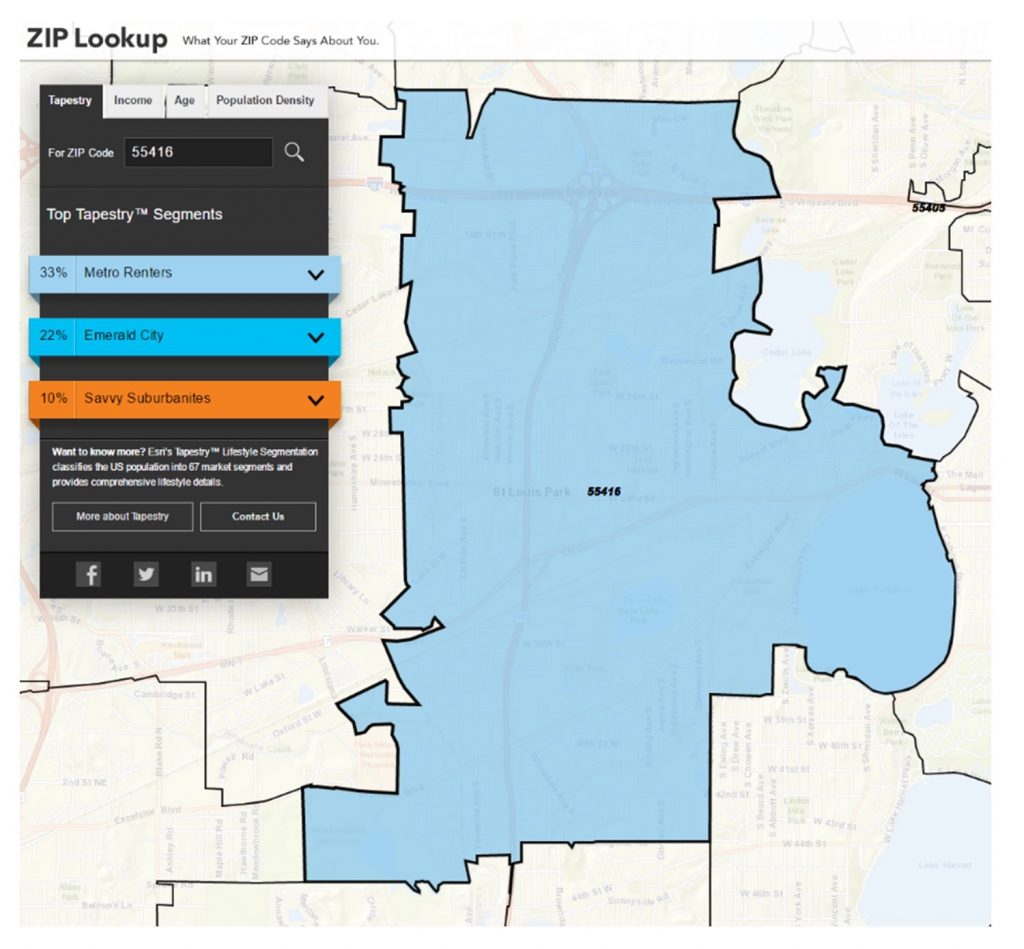
Geodemographics. Esri’s Zip Tapestry website describes the general categories of people living in a given zip code, based on a variety of different data. [4]
These technologies are very helpful to firms because they help narrow down where their customers live. Many college and university students can find elements of their lives in the following description of the “young and restless”:
We’re millennials and coming into our own. We’re young, diverse, well educated, and are either financing our classes or working in professional/technical sales, and office administration support positions. Most of us rent and will move for a job. We live alone or share a place in densely populated areas of large metro areas in the South, West, and Midwest. We can’t do without our cell phones; we text, listen to music, pay bills, redeem coupons, get directions, and research financial information. Not brand-loyal; we shop for the best price. We buy natural/organic food but will also go for fast food. We want to be the first to show off new electronics, but we read online reviews before buying. We go online to bank, buy from eBay, access Twitter and Facebook, and watch TV and movies.
Do you see yourself or someone you know in this description?
8.4 Conclusion
We are steadily moving towards a state of “Total Surveillance,” by which we mean that very few aspects of our lives will not be observed in some way. Many of the necessary technologies are already in place and others are getting better with every day.
Issues around the surveillance society are complicated, and it seems as if they will only get more so as time goes on. When thinking about the good and bad aspects of surveillance, it can help to ask three key questions when considering a given case or scenario.
- What power relations are involved?
- Who controls the technology?
- What are the implications for privacy vs. security?
Resources
For more information about the use of airborne cameras developed for the military in Juarez, Mexico, and Dayton, Ohio, listen to this episode of the podcast Radiolab, “Eye in the Sky.”
To learn more about day-to-day tracking in our lives, read the article by Matthew Hutson in The Atlantic, “Even Bugs Will Be Bugged”
The home page of each of these projects examines and track video cameras. Compare and contrast how each project looks at video surveillance.
Read the article by Adrienne LaFrance in The Atlantic, “Big Data Can Guess Who You Are Based on Your Zip Code.” The article talks about ESRI’s Zip Tapestry.
The Washington Post story Simon Denyer, “China’s Watchful Eye” describes China’s efforts to create a surveillance state. January 7, 2018.
- Guerry, A. M. and A. Balbi, Statistique comparée de l’état de l’instruction et du nombre des crimes, 1829. French National Library. https://commons.wikimedia.org/wiki/File:Statistique_compar%C3%A9e_de_l%27%C3%A9tat_de_l%27instruction_et_du_nombre_des_crimes.jpg?uselang=fr. ↵
- CC BY 3.0. Wikimedia commons; https://commons.wikimedia.org/wiki/File:Surveillance_cameras_Tom_Lee_Park_Memphis_TN_01.jpg ↵
- Fair use. Steven Manson 2015 ↵
- Fair use. Steven Manson 2015 ↵